Author: Tiahn Wetzler
– Senior Content Marketing Editor at Adjust

Mobile fraud is highly problematic for the entire mobile advertising industry. From publishers to measurement partners, fraud damages workflows, drains revenue, renders data inaccurate and throws strategies out the window.
It’s estimated that by 2022, between $44 billion and $87 billion will be stolen from the digital ad marketing industry annually, as a result of mobile ad fraud. Understanding this threat, how it works, and how to best combat it, is vital for marketers. So let’s take a look at how mobile ad fraud works, how fraudsters make money, and what the most effective preventative measures are when it comes to protecting budgets, data, and reputation.
What are the main mobile ad fraud methods?
The primary means by which cybercriminals are incentivized, and ultimately make money, is via click spam, click injection, install farms, and SDK spoofing. This means that fraudsters do their business by either claiming attribution for organic uses, by cannibalizing the advertising of legitimate publishers to steal attribution or by falsifying and spoofing a user for fully artificial conversions.
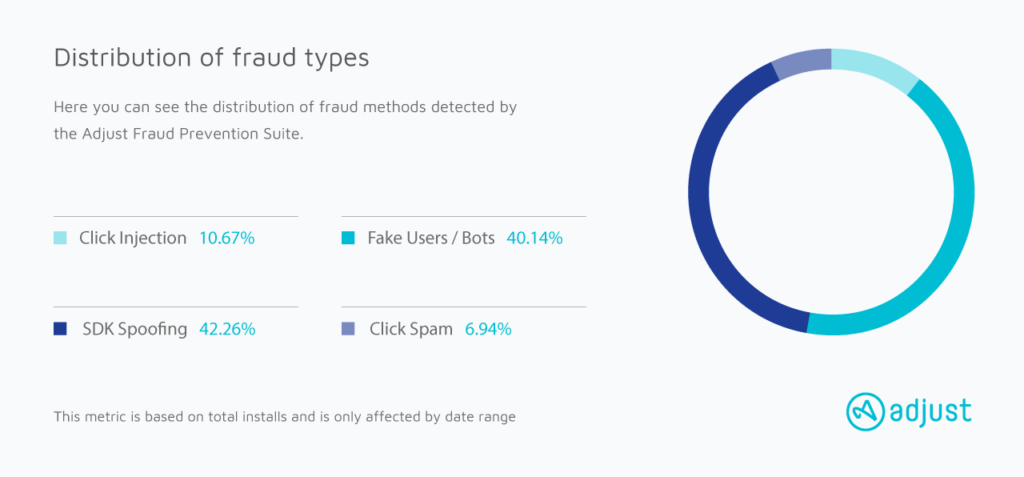
1.Click spam
Also referred to as click flooding or click fraud, claim spamming uses fake clicks to claim credit for an install. This means that fraudsters are able to make it appear as if a user has clicked an ad before installing an app. When a user lands on a web page or an app operated by a fraudster, ad clicks not visible to the user are generated in the background without the user’s knowledge or consent.
The major concern is that fraudsters are awarded revenue for fake clicks, making datasets unreliable. Click spam, for example, results in organic users being incorrectly attributed as users acquired from UA campaigns. The result of this fake data is that marketers are incentivized to invest more spend in campaigns they’ve been led to believe are successful, but are likely generating nowhere near the results they’ve been shown.
Click spam is an extremely common fraud technique affecting mobile advertisers. Last year, for example, Google removed apps created by Chinese Android developer DO Global from the Play Store after a Buzzfeed News investigation revealed a large-scale click fraud operation.
How is click spam detected?
Looking for specific patterns with a statistical approach is the only truly effective detection method that allows rejection before attribution. The Adjust statistical model is called ‘Distribution Modelling’. While investigating the problem of click spam, Adjust found that there was a clear difference in the time distribution of genuine clicks and clicks coming from click spamming sources.
For genuine traffic sources, clicks are attributed with distribution that should look statistically ‘normal’. While the exact shape and size of this distribution will look different depending on the source, it will almost always feature a large number of installs in the first hour followed by a very fast decrease. Installs from click spamming or fraudulent sources, however, usually have a flat distribution. For this reason, installs and click-to-install times will feature a random distribution pattern.
Adjust’s Distribution Modeling filter prevents attributions of installs to spammed clicks by scoring every tracker based on its historical distribution of click-to-install times in order to evaluate statistical occurrences of previous user intent. If Adjust detects click spam, the attribution to a spammed click is rejected and Adjust will look for a legitimate ad engagement to attribute to – if none is available, the install will be considered organic and fraud will be removed from the data set.
From January 1 2020 to July 31 2020, Adjust prevented clients from wasting $178.141.974 of ad-spend.
2.Click injection
Click injection is a clever method by which fraudsters are able to steal attributions from organic and paid channels. By generating clicks that didn’t actually come from users who interacted with an ad, injecting just a single click after a user has made the decision to download a new app is all that is required to undertake the process and take credit for the install. So in this case, the users are real, but the ad-engagements are fake.
Click injection and install broadcasts
When an app is installed on an Android device for the first time, other apps on the user’s device are able to receive the information from a signal that has been broadcast. The purpose of this is to create better connection between apps, making it possible, for example, to use deep linking for streamlined login processes.
Click injection uses one of two distinct exploits to detect when other apps are downloaded and then triggers clicks after the user has already downloaded an app. The fraudster then receives credit for organic installs and those driven by genuine advertising. Similarly to click spam, it’s another method that makes organic users appear to have been influenced by paid campaigns, rendering your data inaccurate.
The most effective way to combat it is by using the Google Play Store’s Install Referrer API and adding new timestamps (install begin and install finish) – this will allow for the rejection of attribution to any ad engagement triggered after the user made the decision to download and use an app. Adjust is able to filter out these clicks by using timestamps.
3.Install farms (Emulation and Instrumentation)
Somewhat less sophisticated than the previous two methods, install farms are real-life locations where real devices are used to manually generate installs. The fraudsters involved will literally click on ads and install apps, and then get paid. The process is easily repeatable as they change IP addresses to make it appear as if large numbers of users are installing the apps being advertised.
A key way to identify installs from device farms is that the users don’t retain and never make any in-app purchases. If users from device farms are mixed with real traffic, however, this can be difficult to identify, considering that day one retention is rarely above 30%.
By looking a bit closer at the routines of these fraudsters, we’re able to see that they have to permanently reset their device IDs to be counted as a new install. Under iOS, for example, the Adjust SDK requires a full device reset to count as another install. This process takes more than 15 minutes and significantly slows down the process for fraudsters working from install farms.
Another marker is the IP address used to send SDK requests – if there is no masking or VPN, the countries of origin will be displayed. If traffic has been moved to profitable markets like the US, the IP addresses used are often registered to data centers and are available on commercial lists, and can be used to deny attribution.
From January 1 2020 – July 31 2020, the Adjust Fraud Prevention Suite rejected a total of 218.025.814 fraudulent installs.
4.SDK Spoofing
When fake installs appear to be legitimate, real device data has most likely been used, and SDK spoofing has likely taken place. When fraudsters break open the SSL encryption between the communication of a tracking SDK and its backend servers they’re able to get the data format they’re spoofing, as a ‘man-in-the-middle’ attack.
At this point, the fraudsters are able to generate installs. Since they are able to read the URLs in clear text format, they are able to learn which parts of the URLs are static, and which are dynamic, enabling them to test and generate fake installs. Once they have access to this information, they’re able to repeat the process. So, real devices are utilized to perform SDK spoofing, but the users, and their engagements, are fake.
At Adjust, we’ve created a cryptographic solution to product our SDK traffic which we call the Signature™ that signs SDK communication packages as our means of combating SDK spoofing. This ensures that attacks don’t work as a dynamic parameter in the URL, which cannot be guessed or stolen, can only ever be used once.
Via these four key methods of mobile ad fraud, fraudsters are able to attack marketing budgets. This means stealing valuable campaign spend and damaging data sets, often rendering them completely inaccurate. By understanding the key ways to identify fraud methods and fraudulent behavior within data sets, marketers and advertisers are equipped with the knowledge required to stop fraudsters from stealing budgets. Adjust’s Fraud Prevention Suite doesn’t just equip app marketers to combat fraud, but enables them to drive growth and ROI by making fraud prevention as simple as flipping a switch.